
Recently the United States Computer Emergency Readiness Team (US-CERT), an organization within the Department of Homeland Security’s (DHS) National Protection and Programs Directorate (NPPD) and a branch of the Office of Cybersecurity and Communications’ (CS&C) National Cybersecurity and Communications Integration Center (NCCIC), encouraged users and administrators to review a recent article from the Federal Bureau of Investigation (FBI) regarding Building a Digital Defense with an Email Fortress.
Are we have discussed in many posts before, phishing — the fraudulent practice of sending emails purporting to be from a reputable entity to induce an individual to reveal privileged information such as a password — remains a major security threat. Within the article, the FBI provides several helpful actions for businesses can take to reduce their risk of being phished, including reporting and deleting suspicious e-mails, and making sure that countermeasures such as firewalls, virus software, and spam filters are robust and up-to-date.
We encourage each of our readers to review the FBI’s guidance and consider whether their organization could benefit from any of the methods of protection provided.
Companies with any questions regarding any of these issues should not hesitate to contact the team at Mintz Levin.
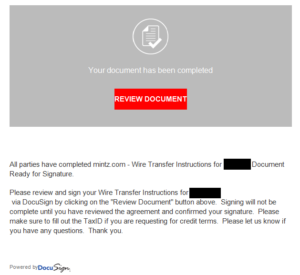

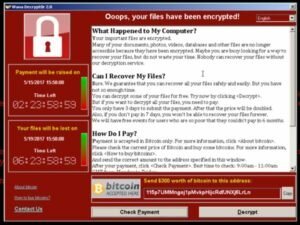 How does ransomware get onto a system generally?
How does ransomware get onto a system generally?  A new month, a new Privacy Monday.
A new month, a new Privacy Monday.